2022 was an eventful information security year. We saw cyber attacks between warring states, whole states going offline after attacks of rogue cybercrime groups, and data breaches in all kinds of businesses (Twitter, Marriot, and Binance, among others). It’s clear that vigilance is vital in protecting against these attacks, and staying informed about the latest threats is crucial. To stay safe, it’s important to implement robust security measures, perform an internal security risk assessment, educate employees on how to spot and avoid dangers, and regularly review and update security practices.
And 2023 seems to be no different; social media scams are creating a new (a)social engineering battleground where adversaries and state-sponsored attackers leverage social engineering techniques as a first step (initial access vector) in large-scale campaigns. These are aimed at breaking into systems, spreading ransomware, or stealing sensitive information. Attacks on critical infrastructure are at an all-time high, deep fake attacks are becoming more and more convincing, and the rise of the metaverse will pave the road to new cybercrimes.

But not everything will be doom and gloom in 2023. A recent survey by ClubCISO shows that the shift to remote and hybrid work has had a positive effect on employee attitudes toward security. With ongoing security awareness training, the research indicates, a good security culture has become the norm for many organizations.
Risk Assessments
When working on information and cyber-security measures, organizations spend a lot of time assessing and mitigating security risks. Risk assessments help to protect against breaches, give an organization critical information about its security gaps, and help to guide security investments. But with the ongoing Work From Home trend, part of the responsibility for cyber-security may have shifted from the organization to the employees’ homes. Performing a personal information security risk assessment at home can help you identify and mitigate potential risks to your personal data and sensitive information. Here are some steps to follow when conducting a risk assessment:
1. Identify Information Assets
Make a list of all the personal and work-related data and sensitive information that you store at home, including financial data, medical records, and personal identification information. Your asset list can include:
- Personal identification information (PII): sensitive data such as your full name, date of birth, Social Security number, passport information, and driver’s license details.
- Financial information: banking information, investment details, credit card numbers, and other financial documents.
- Medical information: health records, prescription information, and other medical documents can be considered sensitive.
- Personal documents: any documents that contain personal information, such as your birth certificate, marriage certificate, divorce decree, and legal contracts.
- Digital assets: any digital information such as photos, videos, music, and important documents stored on your computer, phone, or other electronic devices.
- Passwords and login credentials: These are valuable pieces of information that can grant access to your accounts, which should be kept secure and confidential.
- Intellectual property: any original work you have created such as music, art, or writing, which can be protected by copyright laws.
2. Identify Threats
Identify potential threats to your data and sensitive information, such as malware, hacking, phishing, physical theft, loss, damage, and unauthorized access to your Wi-Fi network. Depending on your work-from-home situation, your list of identified threats may vary. There is much information available on the internet about cyber security threats (e.g. here). You should also take regional and local physical threats into consideration, like the possibility of an environmental disaster, or the crime rate in your area.
3. Identify Vulnerabilities
Identify potential vulnerabilities in your work-from-home environment, in your home network, and devices. These can be weak passwords, outdated software, and unsecured Wi-Fi networks. We already talked about possible vulnerabilities in a former post. A vulnerability list might include the following:
- Weak passwords: one of most common risks, as these can be easily guessed or cracked. This can lead to unauthorized access to personal data and sensitive information. Using the same password for multiple accounts is also a bad practice, as offenders can easily gain access to these.
- Phishing: a type of social engineering attack in which cybercriminals send fake emails, messages, or texts that appear to be from a trusted source to trick users into revealing their sensitive information — such as login credentials or financial information.
- Malware: Viruses, Trojans, and spyware can infect computers and mobile devices, steal personal information, and compromise security. Malware can be spread through email attachments, malicious websites, or downloaded software.
- Unsecured Wi-Fi: Unsecured Wi-Fi networks can expose personal data and sensitive information to hackers. Using unsecured Wi-Fi networks can also increase the risk of malware infections and other types of cyber attacks.
- Lack of updates and patches: Failure to update software and operating systems can leave devices vulnerable to security flaws and exploits. Hackers can exploit these vulnerabilities to gain access to personal data and sensitive information.
4. Determine Risk Level
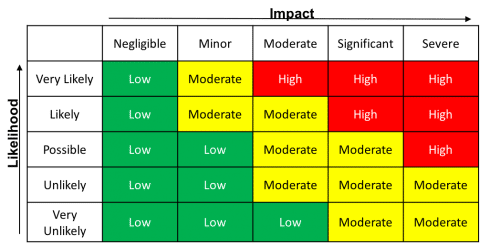
Evaluate the likelihood and potential impact of each identified threat and vulnerability to determine the level of risk. There are many tutorials on how to conduct a risk level determination. You can use a simple risk determination matrix to evaluate a risk rating to act upon. A typical 5×5 matrix is shown below, but you can define your own matrix that fits your personal needs.
You can evaluate the risk level by combining one axis (the likelihood of a certain incident) with the other axis (the impact an incident might have on you when happening). The risk level will be where both axes meet. The impact could be a monetary loss, legal or contractual obligations, or even the loss of your professional reputation. The result from the table tells us how urgently we need to address a recognized threat and vulnerability.
5. Mitigate Risks
Develop a plan to mitigate identified risks by implementing security controls. NIST (the US National Institute of Standards and Technology), defines security controls as “the safeguards or countermeasures prescribed for an information system or an organization to protect the confidentiality, integrity, and availability of the system and its information.” These include:
- Strong passwords
- Two-factor authentication
- Antivirus software
- Updates to software and operating system
- Securing of Wi-Fi networks
- Physical protection of your home office/your physical home itself
Your controls can be physical, like locks on doors, a safe, or any kind of physical access control. Your countermeasures can be technical, like improved authentication methods (MFA), antivirus and anti-malware software, and firewalls. Even things like attending a training or improving information security awareness still count as countermeasures.
6. Monitor and Review
Regularly monitor and review your security controls and countermeasures to ensure they are effective and up-to-date. In organizations, the effectiveness of established information security controls is verified by establishing security metrics (Top 10 Cybersecurity Metrics and KPIs), periodic vulnerability assessments and penetration tests, or internal audits. You can do a personal information security audit by reviewing and updating your assets, threats, and vulnerabilities lists. You can also easily perform penetration tests against your own network by using free services like Intruder. Depending on your experience level with software tools, you might find some advanced open-source options here.
Rinse and Repeat
It’s important to note that a security risk assessment should be an ongoing process, as new threats and vulnerabilities may arise over time. By performing regular risk assessments, you help protect your personal data and sensitive information from potential threats, online and offline.
Don’t let the hackers win — stay proactive in safeguarding your assets.